What is OTP Verification? Comprehensive Guide - 2026
- Weak OTP systems can be weaponized against you. Attackers can trigger massive OTP requests to drain your SMS budget and flood your users with spam.
- While most businesses set 5-minute OTP expiry times, research shows this is too long. Most legitimate users enter OTPs within 1 minute. Longer expiry times mainly benefit attackers attempting brute force.
- Signzy's OTP verification delivers customizable one-time passcodes across 200+ countries with high-volume handling capabilities, securing authentication flows at scale without infrastructure overhead.
Remember the last time you signed up for a new app? That little ping on your phone with a 6-digit code? Seems so simple, yet it’s the same technology that banks, financial institutions, and governments trust to verify million-dollar transactions and official documents.
OTP verification is like having a doorman – except this one creates a unique password for each of your customers, verifies them instantly, then throws it away forever.
Pretty clever, right?
It’s how you can be absolutely certain that people trying to use your service are who they claim to be, whether they’re opening an account or registering a business.
In this guide, we’ll break down exactly how OTP verification powers KYC (Know Your Customer) and KYB (Know Your Business), making it ridiculously easy for legitimate users to prove their identity while keeping fraudulent attempts at bay.
Plus, you’ll learn how to implement it in your business without creating friction in your customer journey.
Related Solutions
What is OTP verification?
OTP verification is a security method used to confirm a user's identity by sending a unique, time-sensitive code to their registered phone number or email address. OTP stands for "One-Time Password", a temporary code, typically 4-8 digits, that expires after a short period (usually 30 seconds to 10 minutes) and can only be used once.
When someone tries to log in, make a transaction, or access sensitive information, the system generates an OTP and sends it to their verified contact method. The user must enter this code to prove they have access to that phone or email, adding an extra layer of security beyond just a username and password.
Types of OTP verification
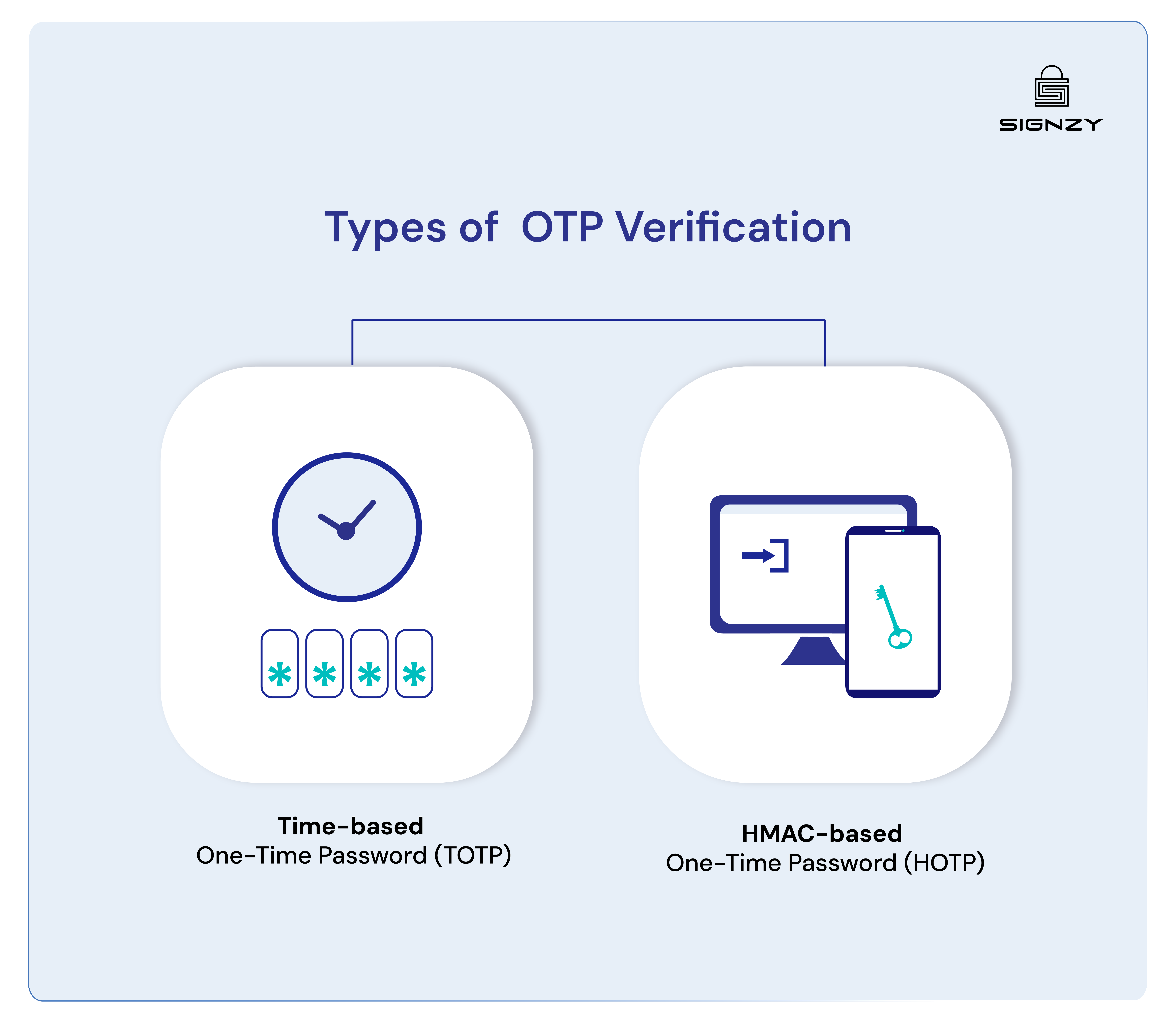
OTP verification can be categorized into two umbrellas: how the code is generated and how it gets delivered.
Generation Methods
Generation methods are the algorithms used to create OTP codes, with three main types:
- Time-Based OTP (TOTP): Generates codes that change every 30-60 seconds based on the current time, used in authenticator apps where codes are calculated independently without transmission
- HMAC-Based OTP (HOTP): Creates codes based on a counter that increments with each use, commonly in hardware tokens, where codes stay valid until used
Generation methods define the technical foundation of your OTP system. TOTP offers the strongest security through time-sensitive codes, HOTP provides flexibility without time constraints, and random OTPs deliver simplicity at the cost of transmission dependency.
Delivery Channels
Delivery channels are the pathways OTP codes take to reach users, with five primary options:
- SMS or WhatsApp Delivery: Sends codes as text messages to registered mobile numbers, delivering within seconds without app installation required
- Email Delivery: Delivers codes to registered email addresses across all devices, cost-effective but slower than SMS
- Authenticator App Delivery: Uses apps like Google Authenticator to generate TOTP codes locally, offering the highest security with no transmission costs
- Voice Call Delivery: Automated calls read codes aloud, serving as backup when SMS fails and providing accessibility for visually impaired users
- Push Notification Delivery: Sends codes as in-app notifications, letting users tap to view or approve instantly with better security than SMS.
The right channel depends on your user base, budget, and security requirements.
How does OTP verification work?
OTP verification follows a straightforward process that combines user action, system generation, secure delivery, and validation to confirm identity in real-time.
User initiates an action requiring verification
The process starts when someone attempts an activity that needs identity confirmation: logging into an account, authorizing a payment, resetting a password, or accessing sensitive data.
The system recognizes this as a security checkpoint and triggers the OTP generation process rather than granting immediate access.
System generates a unique code
The backend system creates a random, single-use code using algorithms that ensure each OTP is unpredictable and unique.
This code is typically 4-8 digits long for ease of entry, though some systems use alphanumeric combinations for higher security. The system also timestamps the OTP and sets an expiration window, usually between 30 seconds and 10 minutes, after which the code becomes invalid.
OTP is delivered to the user's verified contact
The generated code is sent to the user through a delivery channel predetermined by the platform, most commonly via SMS to their pre-registered phone number or to their email address. While we have already discussed the available delivery channels above, here’s a quick gist for reference:
- SMS: Code sent as a text message to the registered mobile number
- Email: Code delivered to registered email inbox
- Voice Call: Automated call reads the code aloud to the user
- Authenticator App: Code generated locally within apps like Google Authenticator or Authy
- Push Notification: Code sent as an in-app notification to the registered mobile device
The delivery method uses the contact information the user provided and verified during account setup, ensuring the code reaches only the legitimate account holder.
The choice of delivery channel depends on the platform's security requirements, target audience, infrastructure costs, and regional considerations. For example, SMS works well in regions with strong cellular networks, while authenticator apps offer higher security for sensitive financial transactions.
User enters the OTP into the system
The user receives the code on their device and manually inputs it into the verification field on the website or app. This step proves they have physical access to the registered phone or email account. The system typically allows a limited number of entry attempts (usually 3-5) to prevent brute-force attacks, where someone tries to guess the code.
System validates and grants access
The backend compares the entered code against the generated OTP, checks if it's still within the valid time window, and confirms it hasn't been used before. If everything matches, the system approves the action and grants access.
If the code is wrong, expired, or already used, the system denies access and may offer to resend a new OTP or lock the account temporarily after too many failed attempts.
This entire process happens within seconds, creating a security layer that's both robust and user-friendly. The time-sensitive nature of OTPs means that even if someone intercepts a code, it becomes useless quickly.
Why is OTP verification necessary?
As we stated earlier, this simple yet powerful system changes how businesses handle identity verification, streamlines customer onboarding, and maintains regulatory compliance – all while keeping fraudsters at bay. Let’s discuss all key use cases in detail.
Compliance and audit readiness
Regulatory requirements grow more demanding each year, particularly in financial services. OTP verification creates clear, time-stamped records of every authentication attempt. These digital breadcrumbs satisfy auditor requirements while making compliance reporting straightforward.
The system automatically logs essential details:
- Authentication attempts and their outcomes
- Timestamps for each verification step
- IP addresses and device information
- Geographic location data, when available
This automated record-keeping changes compliance from a burden into a natural outcome of regular operations.
Know Your Customer (KYC) process
The traditional KYC process often created friction – long forms, document uploads, and waiting periods that tested customer patience. OTP verification changes this narrative dramatically.
When a customer begins their onboarding journey, the system instantly validates their contact information through a quick code verification.
This small step carries significant weight: it confirms the customer’s ability to receive secure communications while establishing the first layer of identity verification.
Know Your Business (KYB) verification
Business verification presents even more complex challenges than individual verification. Each company might have multiple authorized representatives, various contact points, and different levels of access requirements. OTP verification creates a structured approach to this complexity.
When registering a business, authorized signatories receive unique verification codes through their official contact channels. This process not only validates their identity but also creates an audit trail of who accessed what and when.
Account security & fraud prevention
When someone attempts to access an account, the system creates an additional barrier that automated bots and fraudsters struggle to overcome. This real-time verification step proves particularly powerful in preventing unauthorized access attempts.
The system monitors and analyzes verification patterns, spotting potential threats early. Unusual verification requests – like multiple attempts from different locations or outside normal business hours – trigger automated alerts. This proactive approach helps catch suspicious activities before they develop into security incidents.
What are the most common OTP verification problems?
❌ OTP delivery delays or failures: Codes fail to reach users due to carrier issues, poor network coverage, spam filters blocking emails, or incorrect contact information. SMS delivery can take minutes in some regions, while emails may land in spam folders. However, Signzy's multi-channel delivery automatically switches to backup channels (email, voice, WhatsApp) when primary SMS fails, ensuring codes reach users quickly across 180+ countries.
"We switched from our previous OTP provider after they had a 6-hour outage during peak hours. Signzy's uptime has been rock solid. Plus, the delivery speed is noticeably faster. OTPs arrive in 2-3 seconds instead of sometimes taking a minute.” — Security Engineer, CFO (300+ employees)
❌ Rate limiting blocking legitimate users: Overly aggressive rate limits lock out users who genuinely need multiple attempts due to delivery issues. Users requesting resends too quickly get blocked, creating frustration when the original codes never arrived.
❌ User input errors: Users enter codes incorrectly by misreading numbers (0 vs O, 1 vs I), making typos on mobile keyboards, or copying partial codes. Case-sensitive alphanumeric codes and confusing formats increase error rates significantly. Here, if you are using Signzy, you can customize code formats with clear numeric-only options and configurable lengths (4-8 digits) to minimize confusion and reduce entry errors.
❌ Synchronization issues with TOTP: Time drift between servers and user devices causes TOTP codes from authenticator apps to be rejected even when entered correctly. Incorrect device time settings generate codes that don't match server expectations.
❌ Poor error messaging: Generic errors like "Invalid code" don't indicate whether codes expired, were typed wrong, or never arrived. Systems that do not distinguish failure types leave users guessing and repeatedly attempting the same failed approach.
How to implement OTP verification the right way? Best practices explored
✔️ Choose appropriate code length and complexity: Use at least 6 digits for adequate security. Stick with numeric codes for SMS and email since they're easier to read and type on mobile keyboards. Avoid ambiguous characters like 0/O or 1/I.
✔️ Set reasonable expiration times: Configure OTP validity between 5-10 minutes for random codes via SMS or email. Use 30-60 second windows for TOTP codes from authenticator apps. Avoid extremely short times that create unnecessary friction with delivery delays.
✔️ Create clear, helpful error messages: Distinguish between failure types with specific messages like "Code expired" versus "Code incorrect, 2 attempts remaining." Provide actionable next steps in every error rather than leaving users stuck. Show remaining attempt counts before lockout.
✔️ Enable automatic code detection on mobile: Implement SMS autofill on iOS and Android so codes automatically populate input fields when messages arrive, reducing typing errors. Use domain-bound codes on iOS to ensure codes only autofill in your legitimate app.
✔️ Log and monitor verification patterns: Track delivery success rates by channel and region, average validation times, failure rates, and user drop-off points. Set up alerts for anomalies like sudden spikes in requests or unusually high failure rates indicating potential issues.
How does OTP compare to other verification options?
| Factor | OTP (SMS/Email) | OTP (Authenticator App) | Password Only | Biometric (Fingerprint/Face ID) | Hardware Security Keys | Push Notifications | Magic Links |
|---|---|---|---|---|---|---|---|
| Security Level | Medium | High | Low | High | Very High | Medium to High | Medium |
| User Convenience | High - familiar and quick | Medium - requires app setup | High - simple and familiar | Very High - seamless | Medium - requires a physical device | Very High - one-tap approval | High - click email link |
| Implementation Cost | Low to Medium | Low | Very Low | Medium to High | High | Medium | Low |
| Best Use Case | Consumer apps, account recovery, transaction verification | Banking, enterprise apps, security-conscious users | Low-risk applications (increasingly deprecated) | Mobile banking, device unlock, payment apps | Enterprise systems, high-value accounts, admin access | Banking apps, enterprise tools with mobile presence | SaaS platforms, email-based services, and passwordless login |
Best OTP verification system providers
Whether you need basic SMS delivery or a comprehensive verification suite with fraud detection and compliance features, these providers deliver the infrastructure and security your business needs without the complexity of building from scratch.
Signzy
Signzy offers a complete OTP verification solution as part of its broader identity verification platform, available across 180+ countries. The platform supports OTP delivery via SMS, email, and voice channels with customizable code lengths from 4 to 8 digits based on your security requirements.
What sets Signzy apart is the ability to personalize OTP message content for branding and localization, making it ideal for businesses with global operations or specific compliance needs. The API handles high volumes of requests effortlessly, maintaining performance even during peak usage periods, and integrates in just 2-4 days.
“Our old OTP provider failed around 6% of the time. Signzy brought that down below 1%. Integration took maybe half a sprint, which really shocked all of us.” — Backend Engineer, digital platform (190+ employees)
Beyond basic OTP delivery, Signzy provides a comprehensive KYC verification suite that includes document verification, biometric checks, AML screening, and business verification, allowing you to build complete identity workflows rather than cobbling together multiple providers.
Best for: Businesses needing OTP verification plus comprehensive identity verification, companies operating across multiple countries, and financial institutions requiring compliance-ready solutions.
Twilio Verify
Twilio Verify is one of the most popular OTP solutions, offering SMS, voice, email, WhatsApp, and push notification delivery channels. The platform provides built-in fraud detection with anomaly detection algorithms that flag suspicious verification patterns, helping prevent account takeover attacks.
Twilio's global carrier network ensures high delivery rates across virtually every country, and the API is well-documented with SDKs for all major programming languages. The service includes features like rate limiting, customizable message templates, and detailed analytics dashboards showing delivery success rates and user behavior patterns.
Twilio also offers the Authy app for TOTP-based authentication if you want to move beyond SMS. Pricing is pay-as-you-go based on verification attempts, making it scalable for businesses of all sizes.
Vonage (formerly Nexmo)
Vonage provides OTP verification through its Verify API, supporting SMS and voice delivery with automatic fallback between channels. The platform excels at handling international delivery with optimized routing to ensure codes reach users quickly, regardless of location.
Vonage offers workflow customization where you can set code length, expiration times, and the number of retry attempts. The API includes features like PIN fraud protection, number insights to validate phone numbers before sending OTPs, and conversion tracking to understand where users drop off during verification.
AWS SNS (Amazon Simple Notification Service)
AWS SNS provides OTP delivery as part of Amazon's cloud infrastructure, offering SMS and email channels with seamless integration into AWS ecosystems. If your application already runs on AWS, SNS offers the easiest integration path with minimal setup required.
The service benefits from Amazon's global infrastructure for reliable delivery and scales automatically to handle any volume. SNS supports transactional messaging with low latency and provides detailed CloudWatch metrics for monitoring delivery success.
While it lacks some specialized OTP features like built-in verification logic or fraud detection, it's extremely cost-effective and reliable for straightforward OTP delivery. You'll need to build your own verification logic and security controls on top of the delivery mechanism.
💡 Key Takeaway: Signzy stands out for businesses requiring OTP as part of a complete compliance and verification stack, while providers like Twilio and Vonage excel at pure OTP delivery with extensive customization.
💡 Related Blog:
How does Signzy's OTP verification solution work?
Remember how challenging old security systems used to be? Those complex interfaces, delayed verifications, and constant maintenance headaches? Modern OTP APIs have changed this space.
Instead of managing complex infrastructure or handling security updates, businesses simply connect to robust verification systems that handle everything automatically – from generating secure codes to ensuring rapid delivery.
"Handles our volume spikes without breaking a sweat. This Black Friday, we sent 500K OTPs in one day. Signzy handled it effortlessly. Previous provider would've crumbled." — Compliance Director (2000+ employees)."
For businesses, this means eliminating verification delays, reducing support tickets, and creating smooth experiences that customers appreciate. Plus, with pay-as-you-go pricing, organizations only invest in what they actively use, making robust security accessible to businesses of all sizes.
Signzy’s OTP Verification API brings these benefits to life. Whether handling high-volume verifications or ensuring consistent delivery across global markets, the system manages complications while businesses concentrate on growth. Simple to integrate, reliable to run, and ready to scale. Contact us today.
FAQ
How long does OTP verification typically take to implement in an existing system?
What happens if customers don't receive their OTP codes?
Is SMS OTP still secure enough for financial transactions?
How do OTP systems handle global customers across different time zones?

Roshan Kumar
Roshan leads product strategy for Identity and Fraud Verification at Signzy Technologies, where he oversees the development of secure, scalable ID Verification, Automated CKYC, and AI-powered Video KYC solutions for regulated banks and fintechs. With over five years of hands-on experience in KYC and API banking and a strong engineering background, he focuses on building platforms that ensure seamless and compliant onboarding across the BFSI sector. His expertise spans designing and implementing solutions that address evolving regulatory requirements and industry challenges.