Among the questions that can potentially induce an existential crisis is, “Who are you?”. Among the phrases that can answer this question are, “You are who you are”, “You are what you do”, “You are what you eat”, and the optimistic “You are what you want to be”. This blog isn’t a metaphysical exploration of who we all are. But, as residents of the Internet Age, it is an attempt to figure out what constitutes our online identities, how they’re threatened, verified, and protected.
The sum of an individual’s characteristics and interactions on the internet can be said to be their online identity. Every minuscule piece of information about a person on the internet adds to this virtual identity. Since our interaction with different online sites would be different, each site has its own understanding of who a person is.
Amazon knows what products you like to buy. Zomato knows all about your midnight cravings. Google has seen the panicky medical searches made at the slightest hint of a cough. Uber probably knows where you live. Facebook knows your friends just as much as it knows you. Netflix knows what you binge after work, and Spotify knows your workout jam.
This may not give a clear picture of the individual to these platforms, but defines a way to identify them. All of these are an individual’s partial identities, the aggregate of which make up who we are online.
Our online identities are related to a number of facets in the virtual world. The prominent ones are discussed ahead:
Profiles, Cookies, and Footprints
Site Profiles:
For many of the apps and sites we sign up on, we construct profiles. When it is not required to feed some data for the creation of a profile, unbeknownst to us, the site creates a profile for us. This is to distinguish an individual, maintain a record for them, and secure their information. An attribute called an “identifier” is needed to create this automatic profile. The identifier is a way of referring to a set of characteristics. It can be something like a number given by the site, your email ID or a username.
Browser Cookies:
A cookie can be understood as a piece of information sent by a web server for the browser to store. The browser returns the cookie to the server the next time the page is opened. Cookies usually contain at least two pieces of data:
• a unique user identifier
• some information about that user
It’s cookies that preserve the state of a user’s interaction on a site across browser sessions and page reloads. They help in the optimum functioning of the website, and although seemingly innocuous and invisible, cookies can store various data points. If you allow your browser to accept cookies, you are being tracked. For example, sites using embedded Google tools such as the search bar, trace your activity via cookies whose data Google will have access to.
Cookies fall under the purview of data protection regulations such as the GDPR, which is a testament to the personal nature of the data they contain. Explicit consent is now required from the user to allow the cookies to attach themselves to an individual’s browser.
Digital Footprints:
We are constantly leaving behind a digital footprint on the internet. This refers to the traces of data we leave behind on the internet, the primary constituents of which are website cookies and social media activity. This footprint is what is commonly commercialized. Third parties such as advertisers pay for this data, and digital footprints are thus monetized with companies having access to our data. This may lead to:
- Data deduced from footprints used for big data analytics
- Loss of privacy and anonymity
- Information shared with advertisers without our explicit knowledge for targeted advertising
- Malicious activity such as identity theft
Identity Providers
In the technical sense, identity provision can be distilled into three forms:
a) Traditional or retrospective identities: Individuals receive a credential from a third party after a trusted enrollment process. It can then be used to authenticate oneself.
b) Low trust or self-asserted identities: The third party merely issues an identifier to the individual which it can confirm when asked.
c) Behavioral identities: When enough data about an individual is collected by the service providers to decipher that the same person is visiting multiple times.
Google or Facebook have the capacity to act as a trusted identity provider (IdP) by authenticating an individual on behalf of some other online entity that is being signed in to. These are called social IdPs and are accepted across platforms for their convenience, bypassing re-authentication processes. With this possibility, the digital world is shifting from siloed credentials to those that are accepted across platforms. For example, your employee ID cannot be used to identify you at an airport, but your Google account can be used to make a booking through MakeMyTrip.
While this type of identity aggregation makes the onboarding process efficient for individuals, it is also beneficial for advertisers. As opposed to using subsets of data from different platforms, referring to an IdP allows them to:
- Personalize experience
- Provide recommendations
- Preserve customer histories
- Prepare and proliferate hyper targeted ads
However, this gives rise to the problem of panopticism. It is a concept by French philosopher Michel Foucault used to explain a kind of internal surveillance. In this case, the IdP will be able to keep track of each place an individual is authenticating, without them being overtly aware of the data being subliminally collected.
It is evident that social logins are shaping the future of our digital identities. The European Commission has even proposed the idea of using national ID cards to access online services, such as Facebook, Uber and Twitter. A Facebook profile could thus be lobbied as a border-less digital identity. On the flip side, KYC for social media users has been proposed in India as a way to combat trolling online.
The proliferation of aggregated identities reveals the difficulty and need to remain anonymous in the 21st century. This has paved the way for the existence of alternatives like:
- Sign in with Apple, which can authenticate a user using Face ID on their iPhone without turning over any of their personal data to a third-party company.
- Anonymous social apps such as Whisper which functions as any other social media site, except for they are supposed to be completely anonymous. Users are issued a random nickname upon joining which cannot be searched.
Threats to Online Identity
With our use of the internet entwined with our online identity, the aim isn’t to be anonymous anymore, but to control the degree to which subsets of our data are revealed to public and private entities. While it is difficult to be in full control, it is important to be familiar with the existing threats to our online identity.
Data breaches
A data breach is when confidential information is accessed by an entity not having the authorization to do so. It is common for breaches to go undetected, or companies to not reveal to customers that there has been a breach. “HaveIBeenPwned” is a website that lets netizens check if their personal data has been leaked in data breaches. It reveals the company, year, and constituents of the data breaches where one’s data was compromised from an online account. You can then take remedial measures to safeguard your data and be vary of unsafe logins.
Hackers
Hackers use a multitude of ways to reel in victims of identity theft. Two of the most common ones are phishing and keylogging.
- Phishing is the process of deceiving an individual into sharing sensitive information. It involves attaching links or malicious software codes/bits to a non-suspicious medium like e-mail or a Facebook attachment (pictures/audio clips etc). Clicking on the link/attachment will redirect you to an imitation of a trusted website where you would need to provide your credentials. For example, when being phished a careful observation of the URL space in your browser will show that you are not truly on facebook.com, but instead a sly imitation like fac3book.com. An individual’s login credentials, passwords, bank details etc, can then be sold on the blackmarket, used to steal identities or commit bank fraud.
- Keylogging is the retrieval of information through the act of covertly recording keystrokes of a device user. An attacker can use keylogging to intercept sensitive information such as passwords and credit card numbers. A preventive measure is using a virtual keyboard when logging in or carrying out transactions online.
ISP Tracking
Internet Service Providers store the logs of IP addresses and session timings for billing and legal purposes. However, it can be used for questionable purposes as well:
- Data retention, whistleblower Edward Snowden revealed the National Security Agency requested information from ISPs in the US for surveillance purposes
- Data monetization, selling of personal data (this is legal in some countries)
- Bandwidth throttling, in areas where net neutrality is threatened
- Monitoring, for torrents and illegal file shares, copyright infringements
Surveillance
While citizens have a right to privacy in India, constitutional provisions are not yet in effect to question government surveillance of personal data. Excesses of government surveillance, and exceptions in personal data protection laws can lead to aspects of one’s online identity being used against them. It is imperative to hold our governments accountable to privacy demands. The epitome of surveillance is China’s social credit system which tracks individual, corporate, and government behavior across the country in real time to build a database on its citizens.
Verifying Online Identity
While the privacy of our identity is a concern, on the flip side banks and fintechs are concerned with verifying this identity. With a multitude of transactions happening online, verification of our digital identities is imperative.
A digital identity comprises of two forms of information:
- Digital attributes: Email address, date of birth, government issued ID, biometrics, login credentials etc.
- Digital activities: Likes and comments of social sites, purchase history, photos on Instagram etc.
For the most part, the verification of an identity is done by authenticating digital attributes.
The classic method to gain an acceptable level of assurance that the identity of an online customer matches their real-world identity is a three part paradigm which includes verifying:
- Something the individual knows (eg. password/ security question)
- Something the customer has (eg. identity card)
- Something the customer is (eg. biometrics, such as a fingerprint)
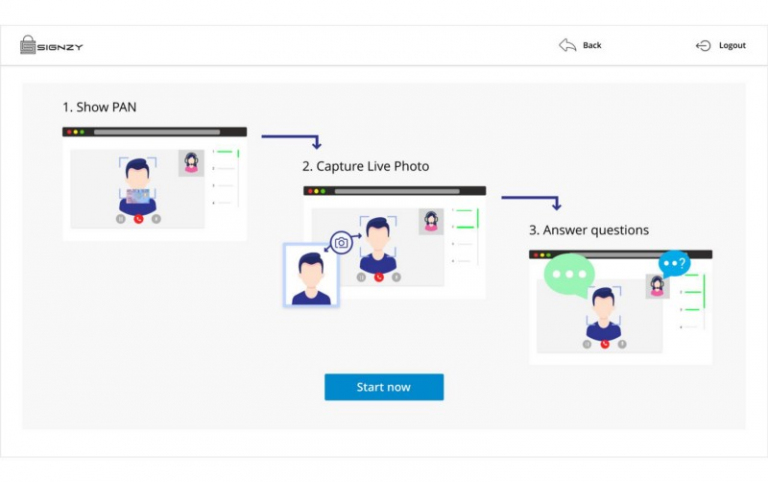
Banks may require more information for security reasons. One way is to observe and an individual’s behavioral data such as login habits. When there is an anomaly, the bank can then alert the customer and verify activity to prevent fraud.Digital identity verification service can encompass social media identity as a layer of verification. For example, BlaBlaCar and Ola request sharing of social media profiles as an additional layer for a quicker KYC process.
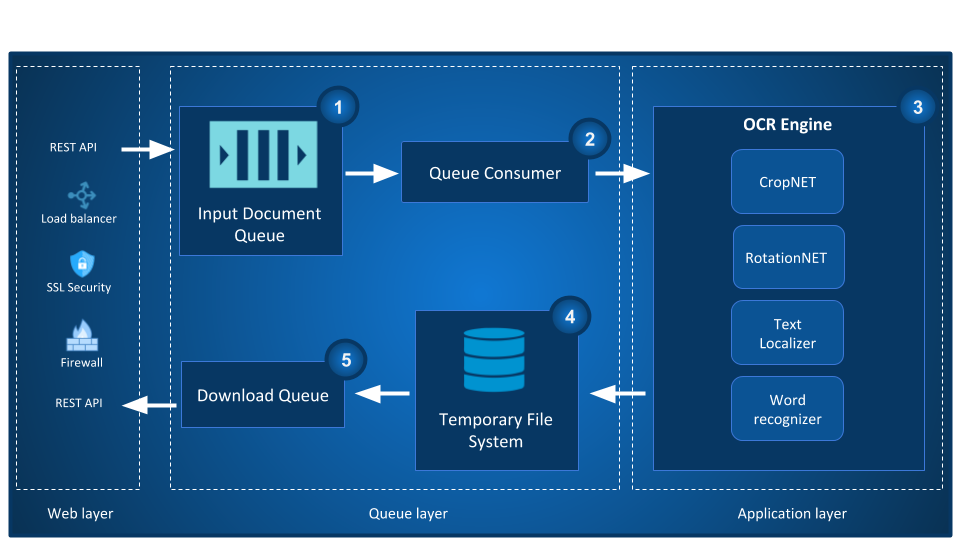
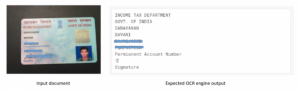
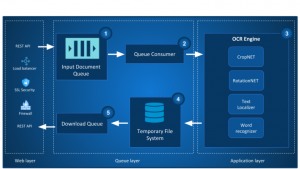
More than seventy financial institutions including 7 major banks in India trust Signzy’s RealKYC and VideoKYC solutions to make the entire process simple, secure, and compliant.
Protecting Online Identity
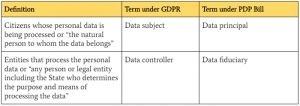
While it seems as if the virtual walls of the internet have eyes and ears, it is not difficult to protect your data. Although it appears as if the government and private companies alike are after your personal data and online identity, with data protection regulations in effect, no one can access your data without your knowledge and in some places, your consent. (To read more on the regulations in place in the EU and India, you can take a look at our article comparing the GDPR and PDP Bill)
Here are a few ideas on how to safeguard your private information:
- Inspect privacy policies before granting permissions
- Change passwords often
- Avoid unprotected or public Wi-Fi networks
- Have a primary and secondary email. When logging in to a new site you do not trust, use a secondary email which is not linked to any other accounts with personal information
- Use a Virtual Private Network (VPN) to access the internet. This masks your IP and ensures your trail is encrypted, dissuading any malware to follow into your device.
- Try not to save passwords on your browser. This can protect you from malicious cookies that may get access to the rest of your saved passwords.
Whether you know who exactly you are or not, you’re now adept to protect who you are in the digital world.
About Signzy
Signzy is a market-leading platform redefining the speed, accuracy, and experience of how financial institutions are onboarding customers and businesses – using the digital medium. The company’s award-winning no-code GO platform delivers seamless, end-to-end, and multi-channel onboarding journeys while offering customizable workflows. In addition, it gives these players access to an aggregated marketplace of 240+ bespoke APIs that can be easily added to any workflow with simple widgets.
Signzy is enabling ten million+ end customer and business onboarding every month at a success rate of 99% while reducing the speed to market from 6 months to 3-4 weeks. It works with over 240+ FIs globally, including the 4 largest banks in India, a Top 3 acquiring Bank in the US, and has a robust global partnership with Mastercard and Microsoft. The company’s product team is based out of Bengaluru and has a strong presence in Mumbai, New York, and Dubai.
Visit www.signzy.com for more information about us.
You can reach out to our team at reachout@signzy.com
Written By:
Signzy
Written by an insightful Signzian intent on learning and sharing knowledge.