What is a High-Risk User? How to Detect & Manage in KYC Compliance
- 70% of grand corruption cases studied by the World Bank involved shell companies, often used by high-risk users.
- High-risk users, including those who fit the profiles of Politically Exposed Persons (PEPs) or those involved in high-stakes industries like gambling, frequently require special monitoring and in-depth checks.
- High-risk users are often linked to larger criminal organizations or illicit activities, making them especially challenging to monitor within the typical compliance framework.
Some users are routine. Steady transactions, predictable behavior, nothing out of place. Others? They don’t follow the usual patterns. Their details check out, but something about how they move funds, open accounts, or interact with the system feels different. Not necessarily wrong, just… off.
That’s the challenge with high-risk users.
They don’t always look risky at first glance, but they do have slightly abnormal patterns.
And you need to see what’s beneath the surface before it becomes a compliance hurdle.
This guide will tell you exactly how, step-b-step. Best part? You just need 8 minutes to go through this guide.
Let’s start by understanding nuts-and-bolts.
Related Resources
High-Risk Users, quick definition
A high-risk user is an individual or entity flagged due to potential legal, financial, or regulatory threats. These users exhibit characteristics that increase the likelihood of fraud, money laundering, or non-compliance with financial regulations.
While there are endless factors, they are typically identified based on five main factors:
- Past fraudulent activity
- Involvement in high-risk industries
- Presence on sanction lists
- Transactions in high-risk jurisdictions
- Suspicious transaction patterns.
Businesses dealing with such users must apply enhanced due diligence (EDD) to mitigate risks and ensure compliance with AML and KYC regulations.
Categories of High-Risk Users
Some high risk users raise concerns due to their background, others because of their transaction behavior, and some simply operate in industries with higher scrutiny.
As not all high-risk users pose the same challenges, understanding the risk of each is necessary to find suitable treatment. Here’s a topline overview of some of common high-risk categories, their indicators, and potential risks.
| Category | Indicators | Risk |
|---|---|---|
| Politically Exposed Persons (PEPs) | – High-ranking government roles. – Close family/business ties to politicians. – Transactions involving public funds. | Corruption, bribery, financial misconduct. |
| Sanctioned Individuals & Entities | – Listed on OFAC, UN, FATF, or EU sanction lists. – Ties to blacklisted organizations. – Financial activity in sanctioned countries. | Legal penalties, frozen assets, regulatory scrutiny. |
| High-Risk Jurisdiction Users | – From FATF grey/blacklisted countries. – Using offshore tax haven banks. – Bypassing geo-restrictions via VPNs. | Increased AML risks, money laundering concerns. |
| Fraudsters & Identity Manipulators | – Fake KYC documents, mismatched data. – Disposable emails, virtual numbers. – Multiple accounts linked to the same device/IP. | Money laundering, account takeovers, payment fraud. |
| Money Mules & Shell Companies | – High-volume transactions with no business purpose. – Newly registered businesses with little activity. – Moving funds between multiple accounts. | Money laundering, financial fraud. |
| Crypto & Privacy Coin Users | – Using Tornado Cash, Monero, or mixers. – Large withdrawals to unknown wallets. – Avoiding KYC via decentralized platforms. | Illicit fund transfers, regulatory non-compliance. |
| High-Risk Industry Participants | – Involved in online gambling, betting, or adult content. – Unregistered money service businesses (MSBs). – High chargeback risks. | Financial crime, regulatory scrutiny, compliance risk. |
Key Regulations for High-Risk Users
Governments and regulatory bodies worldwide have established frameworks to ensure businesses implement strong KYC and AML measures when dealing with high-risk users.
Some key regulations include:
- Financial Action Task Force (FATF) – Sets global AML and counter-terrorism financing (CFT) standards, requiring risk-based approaches for high-risk users.
- USA PATRIOT Act (USA) – Mandates enhanced due diligence (EDD) for financial institutions dealing with suspicious users and foreign transactions.
- Bank Secrecy Act (BSA) (USA) – Requires businesses to monitor, report, and prevent money laundering activities through Suspicious Activity Reports (SARs).
- EU Anti-Money Laundering Directives (AMLD 4, 5, & 6) – Strengthens AML requirements, expands PEP screening, and enforces strict KYC rules across the EU.
- Crypto Travel Rule (FATF) – Mandates crypto exchanges and wallet providers to share KYC details for high-value transactions to prevent illicit activity.
- Basel Committee on Banking Supervision (BCBS) Guidelines – Establishes global AML/KYC compliance standards for banking institutions.
Next, let’s now see how to identify and conduct due diligence of high-risk users.
Steps to Identify and Conduct Due diligence of High-Risk Users for KYC verification
Not every high-risk user looks the part. Some clear basic checks but show inconsistencies over time. Others have verifiable identities but operate in ways that raise concerns.
Therefore, you need a process that filters as many high risk users as possible. Below’s a reference process you can plug and use (you can always edit as per your needs).
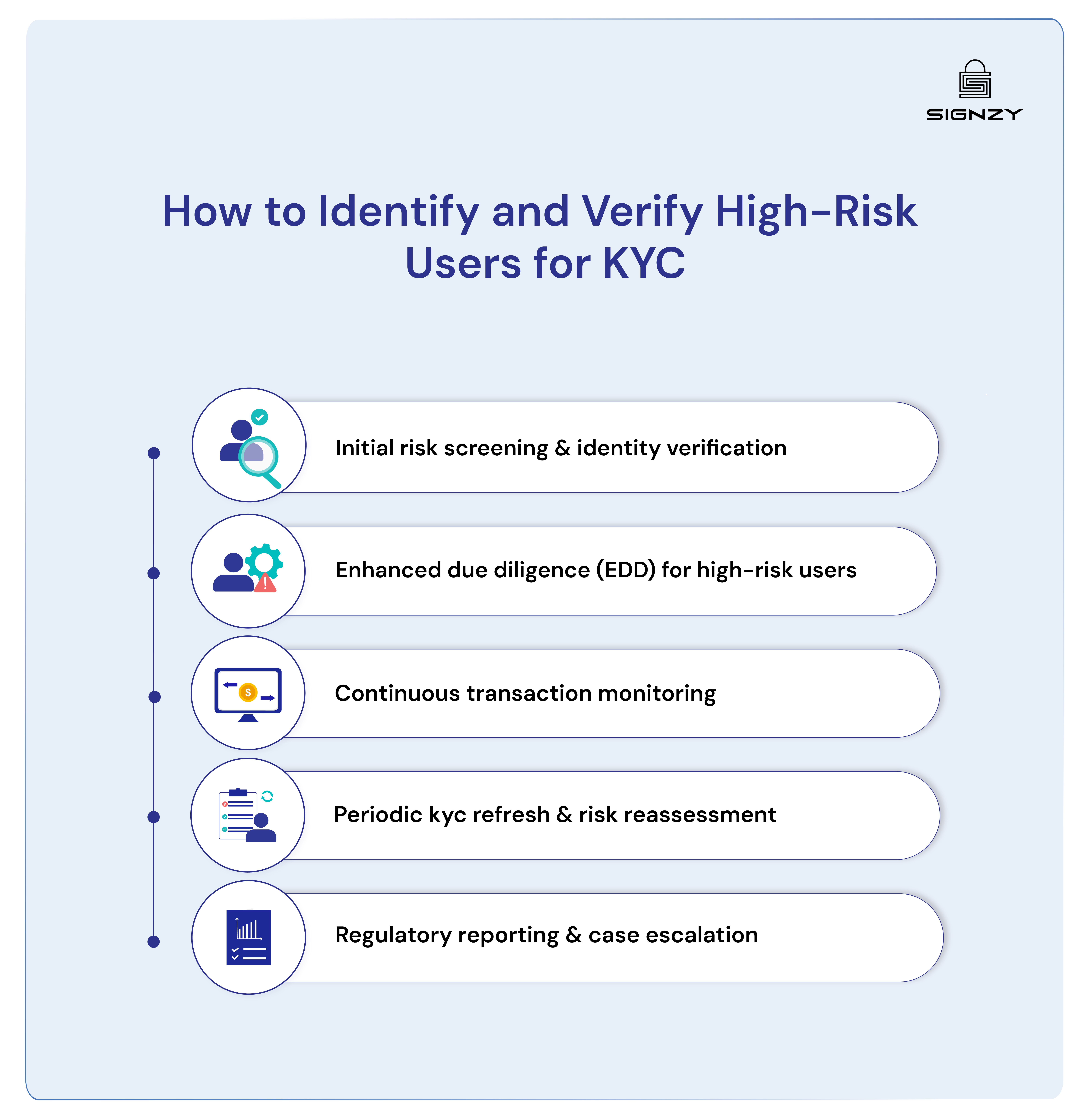
1. Initial Risk Screening & Identity Verification
Before onboarding, users must be screened against known risk indicators. Basic KYC checks involve verifying identity documents, facial recognition, and address confirmation. Watchlist screening helps detect users linked to sanctions, fraud, or politically exposed individuals (PEPs).
If a user triggers a red flag, they require Enhanced Due Diligence (EDD) before approval. This step ensures a deeper investigation into their background and financial activities.
2. Enhanced Due Diligence (EDD) for High-Risk Users
EDD applies to users with higher risk profiles due to their industry, location, or transaction behavior. This involves verifying the source of funds, assessing business legitimacy, and conducting media checks for negative mentions.
- Source of Wealth Analysis – Bank statements, tax returns, and legal contracts must justify large transactions.
- Business Due Diligence – For corporate clients, verifying shareholders, operational history, and regulatory status is necessary.
- Ongoing Monitoring – Even after onboarding, high-risk users must be flagged for continuous reviews.
EDD users face restricted access until the verification process is completed. If risk factors persist, service may be denied.
3. Continuous Transaction Monitoring
High-risk users require ongoing surveillance to detect suspicious activities. Large, frequent, or structured transactions without clear purpose are red flags. Users sending or receiving funds from high-risk jurisdictions or crypto mixers also need close scrutiny.
Real-time AI-driven monitoring can identify abnormal patterns, while compliance teams review flagged cases manually. If a pattern of suspicious activity emerges, the case must be escalated.
4. Periodic KYC Refresh & Risk Reassessment
A one-time KYC check is insufficient for high-risk users. Regular updates ensure their risk status remains accurate. High-risk users should undergo full reverification at least once a year.
Risk scoring systems help automate reassessment by adjusting user profiles based on transaction behavior. If new risk factors emerge, additional due diligence is required. Manual compliance audits provide another layer of security for high-value accounts.
5. Regulatory Reporting & Case Escalation
When a high-risk user is suspected of financial crime, regulatory bodies must be informed. Reports such as Suspicious Activity Reports (SARs) are filed if transactions indicate fraud, laundering, or ties to illicit networks.
Failure to report can result in heavy fines or legal consequences for financial institutions. If a user is confirmed as high-risk, they should be blacklisted and denied access to financial services.
Taking the help of technology like Signzy's API
A good compliance process does two things well.
- Detects risk
- Moves fast
But as fraud gets more sophisticated, manual reviews alone can’t keep up.
Technology fills the gap, making high-risk detection sharper, faster, and more scalable.
Here’s how some solutions can help you with managing compliance when dealing with high risk users:
- Criminal Screening APIs – Checks users against global fraud, crime, and sanction databases to flag potential risks early.
- PEP Screening APIs – Identifies politically exposed persons to ensure transactions comply with anti-corruption laws.
- Identity Verification APIs – Uses AI-driven document authentication and biometrics to verify users with high accuracy.
At Signzy, we have built a unified compliance API suite that help businesses onboard users faster while staying fully compliant. Our APIs integrate seamlessly, automating KYC, AML, and fraud detection without disrupting customer experience. Learn more today.
FAQ
1. What is the difference between KYC and AML compliance?
2. Why is PEP screening necessary for financial institutions?
3. Can APIs replace manual compliance checks entirely?
4. What types of businesses need high-risk user screening?

Gaurav Gupta
Gaurav Gupta is the Global Product Head at Signzy, leading the strategy and development of the company’s KYC, KYB, AML, and digital onboarding products used by banks, fintechs, and financial institutions across global markets. He specializes in building scalable compliance and verification platforms, transforming complex regulatory and risk workflows into seamless, automated product experiences. Gaurav works at the intersection of product, engineering, and AI.