Identity Verification v.s. Identity Authentication: Similarities and key differences
April 15, 2024
7 minutes read
The issues of data breaches and ID theft are becoming increasingly critical for most organizations nowadays.
The Identity Theft Resource Center (ITRC) statistics revealed that the number of data breaches reported between the first three quarters of 2021 was 17 percent higher than the entire figure reported for the previous year.
The ITRC also estimates that there will be an increasing number of identity frauds potentially as criminals look to attack payment apps, digital wallets, peer-to-peer platforms, and other payment methods.
Moreover, a lot of criminals are focused not on stealing personal information but rather on invading corporations and finding into the vast pools of identity information.
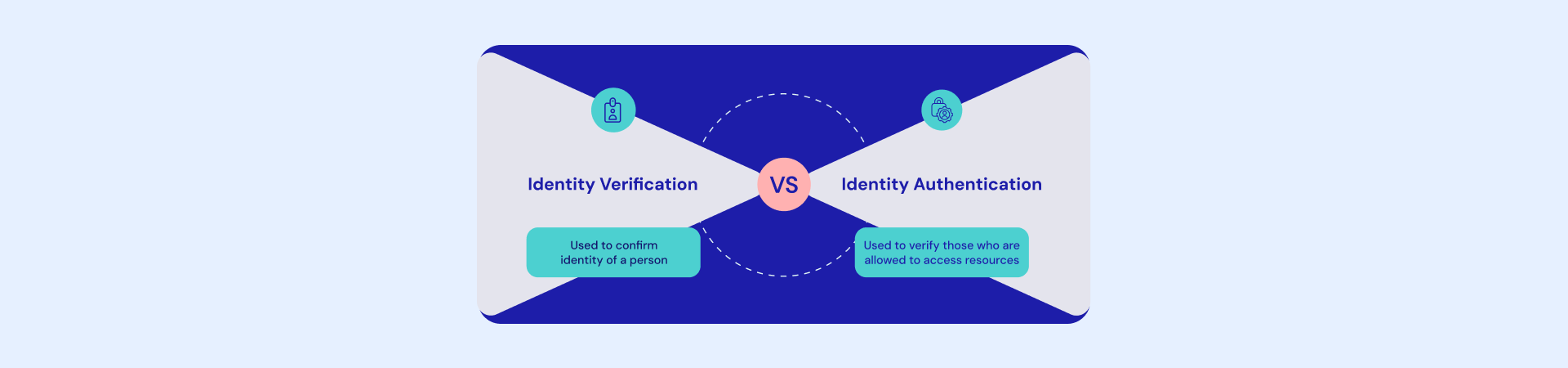
This consequently makes it all the more imperative for businesses to be conscious of who they are engaging each time they encounter a customer. To accomplish this goal, two approaches work in tandem: identity confirmation and identity authentication.
What is Identity Verification?
Identity verification is a one-time process in which the identity of a person or entity is confirmed.
It is often confused with identity authentication whose main function is to prove that the individual using the passport is the person they claim to be. This not only prohibits the occurrence of fraudulent actions but also ensures tight security.
Some techniques are used in identification verification, such as IDs and utility bills provided by the government and passports.
1. Government-Issued ID Documents: such documents as driver’s licenses and passports not only give official evidence of a person’s identity but verify his/her name, age, address, and other personal data.
2. Utility Bills: Verifying an applicant’s address can also be done through utility bills, either water or electricity. They become very instrumental when someone lacks government-issued identity cards. The utility bill information, which includes the person’s name, address, and the date the bill is prepared, could be compared with the information stated by the individual to ascertain accuracy and continued consistency.
3. Other Methods of Identity Verification: The fact that not all organizations may accept utility bills as the most common form of identity verification should also be highlighted in all government-issued IDs (IDs) and passports.
There is the possibility that some of the organizations will make use of the additional methods used for identity verification such as biometric data, financial information, or electronic verification services that provide more information about the identity of an individual.
What is Identity Authentication?
Authentication of identity involves the verification of a person who is allowed to view or act upon the data and resources.
Differing from identity verification which provides validation of whether an individual is the one he/she claims to be, identity authentication focuses on the confirmation that the individual has appropriate permissions and rights to obtain valuable data or systems access.
There are different methods of identity validation which are login credentials, fingerprint recognition, and face recognition.
Login Credentials: For example, login details such as a username and password are conventionally used to verify that a person is who they say they are, and in turn, to permit entry to online accounts or systems.
Biometric Methods: Likewise, biometric techniques including fingerprinting and facial recognition possibly are applied to authenticate an individual and to enable him or her to save the systems that are protected.
The distinction between identity authentication and identity verification as a key factor should be taken into consideration. On the one hand, both of these are important factors that they should make use of to ensure everybody’s trustworthiness and sustainability. Nevertheless, they are inverse to each other and emphasize different features of identity management.
What are the Differences?
Though identity assurance and identity authentication may be related, they carry completely different purposes set over different approaches.
Here’s a breakdown of the key differences:
Focus: Identity verification, which aims to determine the identity of a person or entity, is different from further stages of identity authentication that provide evidence for access to information and resources.
Data Type: Identity verification as its name implies establishes an identity online by linking it with the offline identity.
For this purpose, organizations normally rely on data like ID, selfies, or liveness tests, which are tied to people’s physical identity. To explain the situation in a different way, companies working with verification systems will be less anxious about who is logging in each time because they already know it is the person and not her/his friend handing over the password.
As a result, such a method frequently uses data that doesn’t always connect with the individual’s genuine identity like passwords, information based only on knowledge, and so on.
Frequency of Collection: The verification and authentication may also involve when users are signing up for accounts or when they perform their first-ever transaction. It can also occur when users are accessing their accounts or business services that they had previously employed. The way and amount of data collection depend on many factors such as the company’s business which is to exact the degree of the risk and the applicability of regulatory compliance.
Trust which is an integral part of the online experience will maintain intactness through the access controls and authentication process.
If clients can rely on the fact that your organization has them covered with regard to data protection, verification, and authentication, then they are more likely to entrust your platform with data such as financial or personal documents or even medical information.
Implementing solutions that damage user data verification speed, and accuracy will also boost the probability that this process will be of interest to individuals will who continue working with you in the future.
Risks posed by Identification Verification and Authentication
Whether persons validate their identity and authentication or not is a critical security team aspect of security but is, at the same time, full of risks. Here’s a breakdown of the risks associated with each process:
Identity Verification Fraud
Fake identity: It is possible that criminals can employ false/lota documents (an ID card, a passport, bills of utility) to create a non-existent ID.
Synthetic identity: By assembling the Raw material from all sources (e.g. Social Security numbers with various names), criminals can make a new passport. This new passport appears to be a valid one.
Impersonation: Acting as someone else (customer, position of authority) to obtain confidential information or to incapacitate the system.
Identity Authentication Fraud
Password cracking: At the risk of guessing or stealing passwords for accounts.
Phishing: Fake emails or websites pretending to be legitimate are fallback defenses for impersonators to lure users into disclosing login credentials.
Biometric spoofing: To avoid biometrics security (fingerprints, facial scans) false data is used.
These criminal activities can not only cause financial loss, but lead to identity theft, and create security threats or data breaches.
The future of Identity Verification: What to expect?
The future of identity documentation has shifted to digital. Digital identity documents are being now accepted by clients as well as more and more governments creating different types of digital identification i.e. digitizing driving licenses or ID cards and testing cyber security software has made online verification and authentication systems standard among companies.
Signzy has a whole suite of tools to help with the identity verification of your customers. Our ID verification APIs include DL Verification, Optical Character Recognition (OCR), Liveness Checks, Passport Checks, and more.
These APIs can help your business improve its ID verification process and aren’t too complex either, so your customers do not drop off during the onboarding process. Signzy offers all of these tools, and more, at the most economical rate in the industry. So if you’re looking to keep your business’ identity verification up to date, visit our website and learn more!